Single Sign-On with Azure AD
Setup single sign-on (SSO) with Microsoft Entra ID
To set up SSO in AppNavi with Microsoft Entra ID, follow the steps below,
When carrying out this configuration, open the AppNavi portal and Microsoft Entra ID in separate tabs.
Step# 1 Register and create a new Application in Microsoft Entra ID
Register and create a new application in Microsoft Entra ID
-
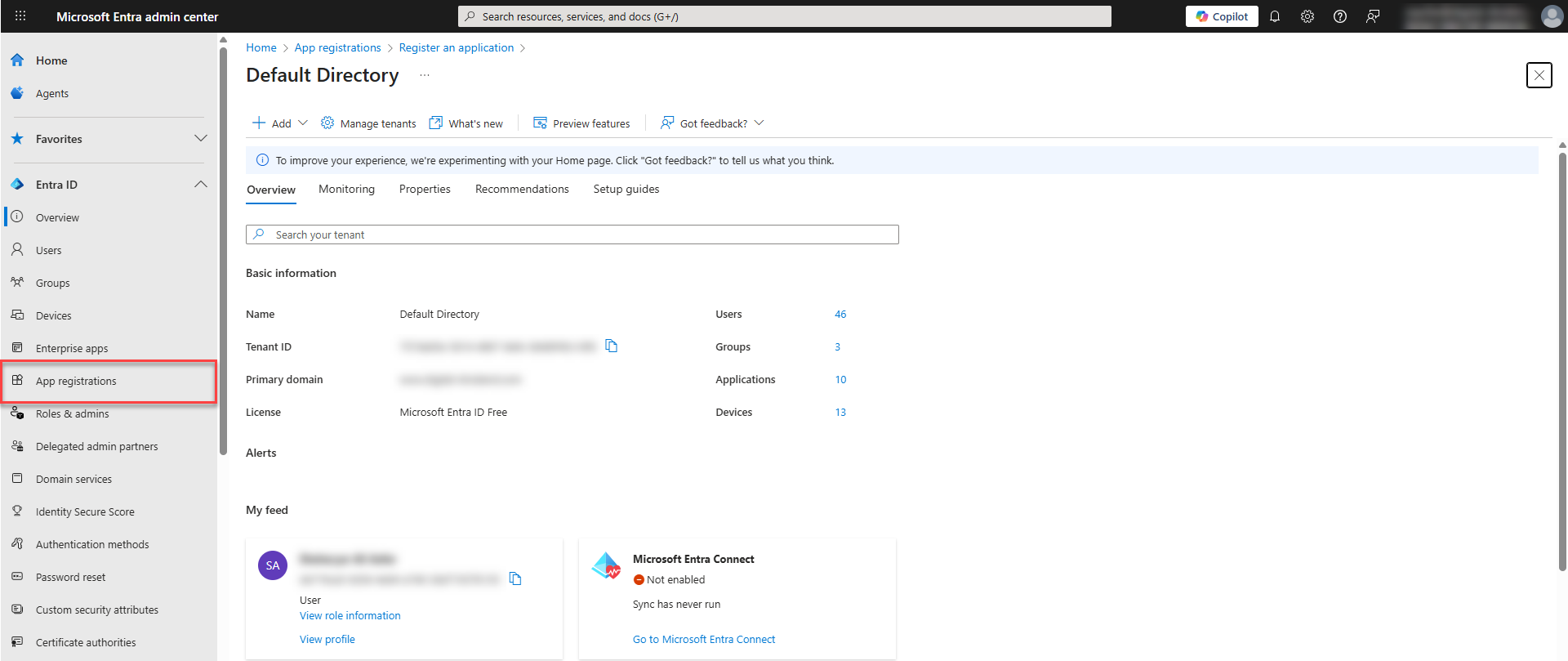
In the Microsoft Entra admin center, go to the main menu and clickEntra ID and then App Registrations.
-
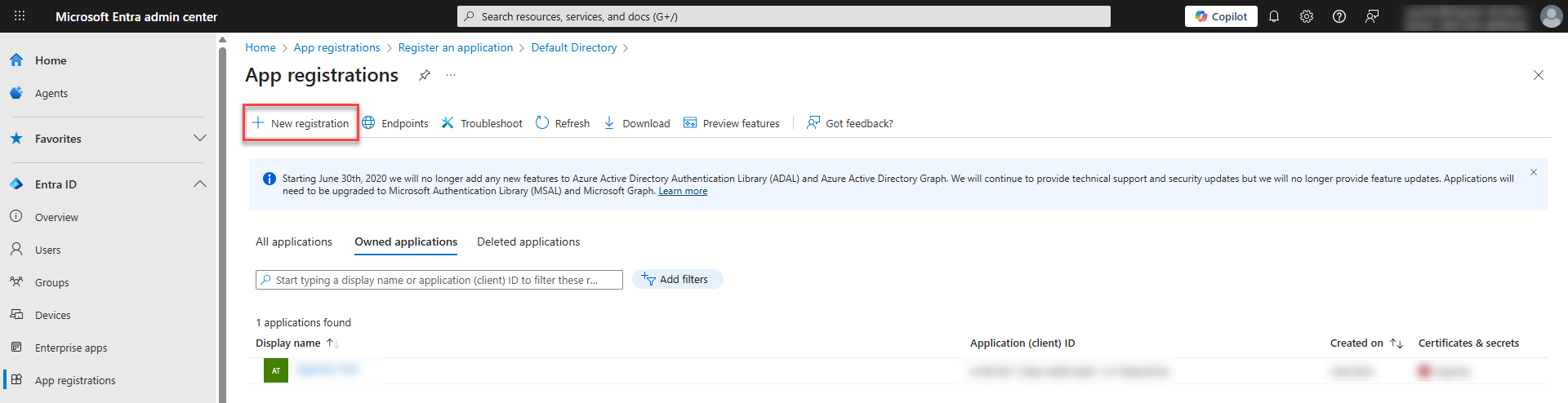
To register a new application for AppNavi, click New Registration.
-
In the Name field, enter a name for the application, for example, "AppNavi SSO".
-
Under Supported account types, select the account type that can use the application or access the API.
-
Click on Authentication from the side menu of the app created.
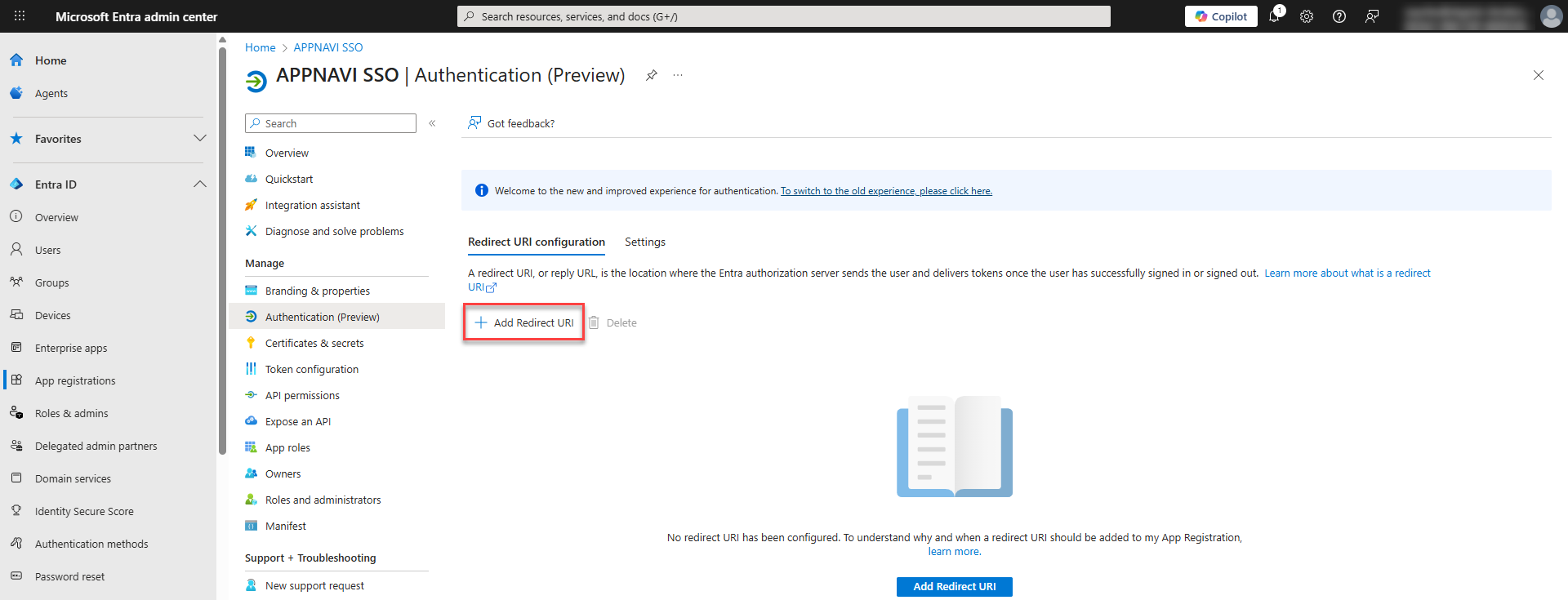
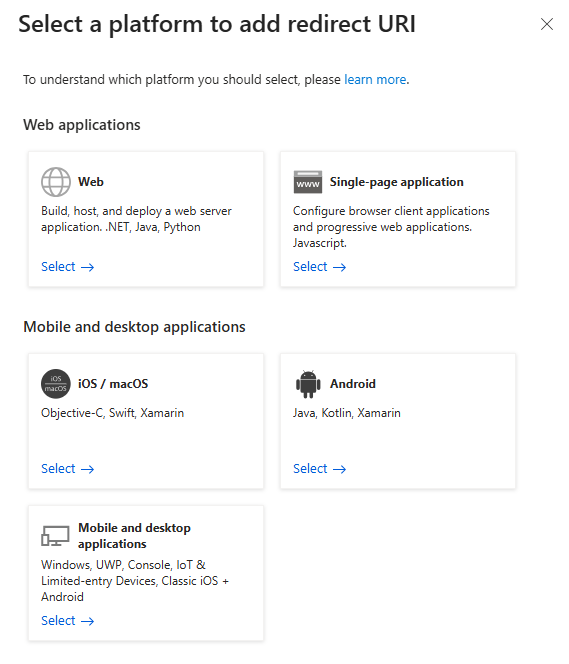
- Click on Add redirect URL and select the platform to add the URL.
- Make sure to check both Access Tokens and ID Tokens.
- In the AppNavi portal, go to Settings > OAuth.
- Copy the URL from the Callback URI field.
- Return to Azure AD, Paste the callback URI that is copied from the AppNavi portal into the field under Redirect URI.
- Ensure that the Web is selected from the drop-down menu as the redirect type
- To register the application, click Register.
A message will display to confirm that the application has successfully been created and you will be taken to the new application.
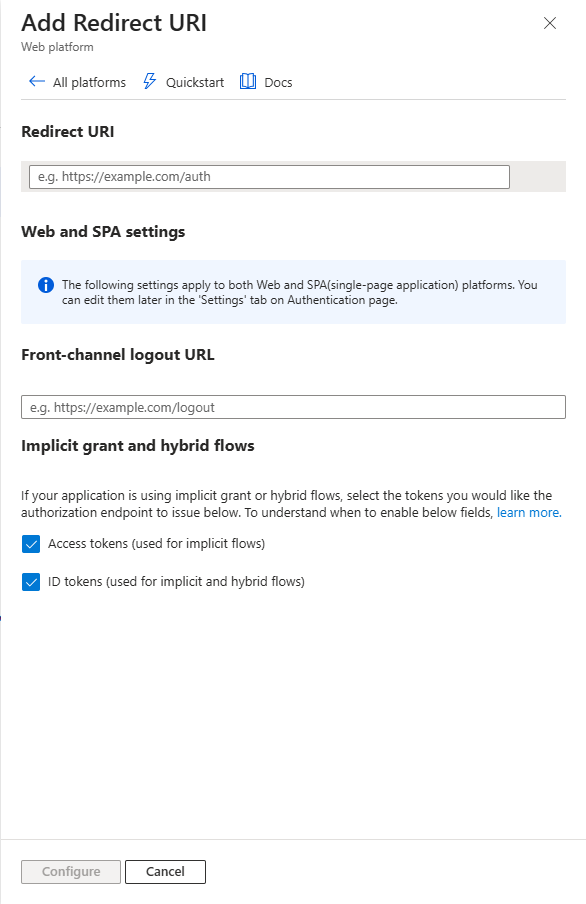
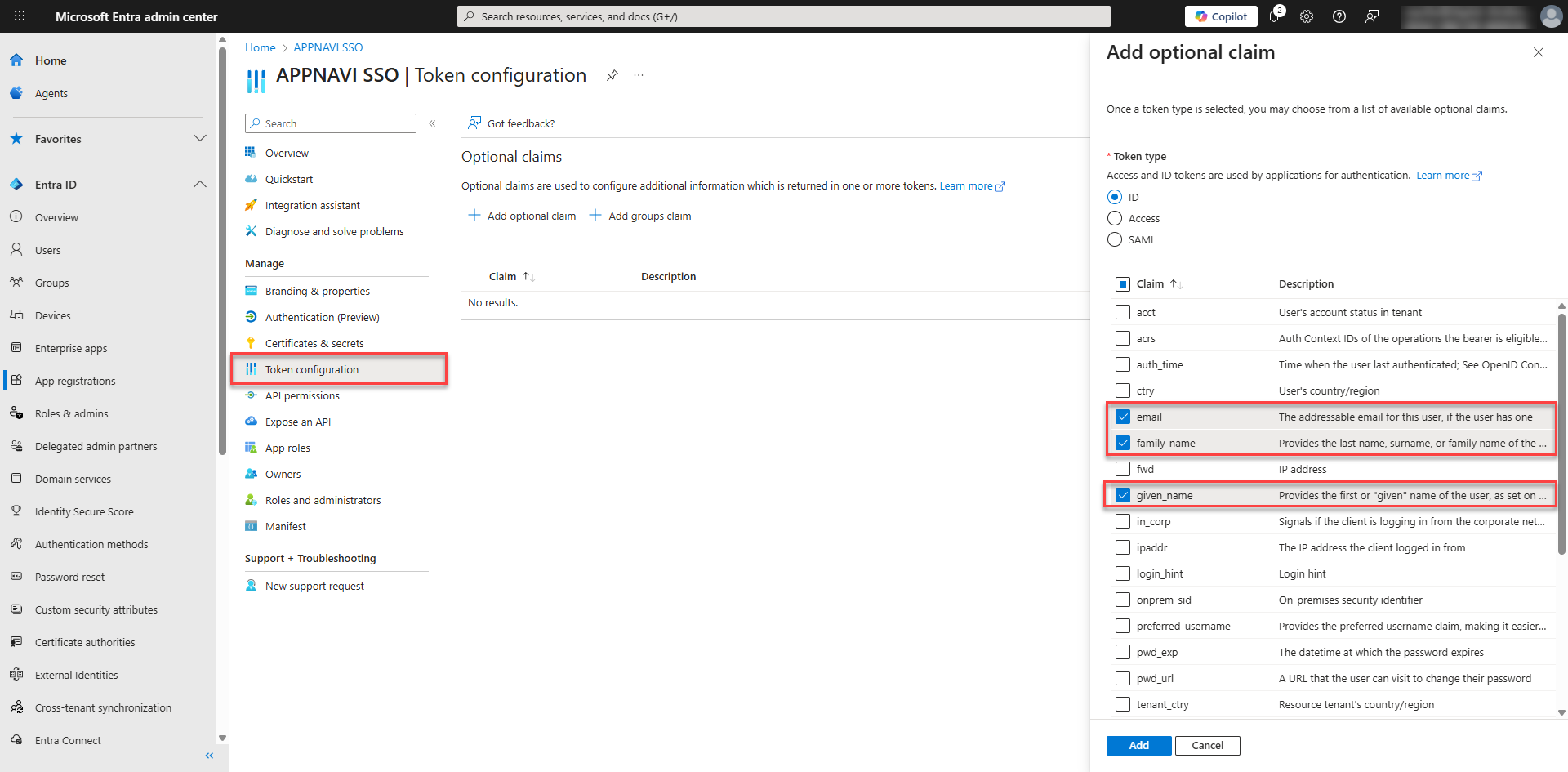
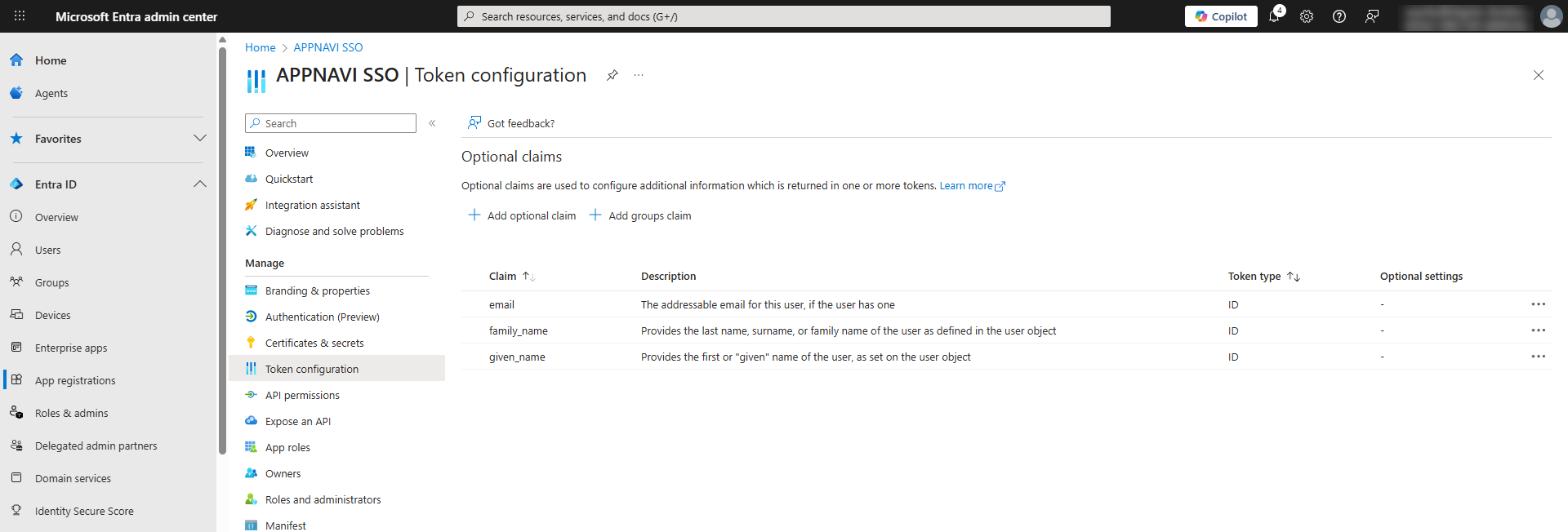
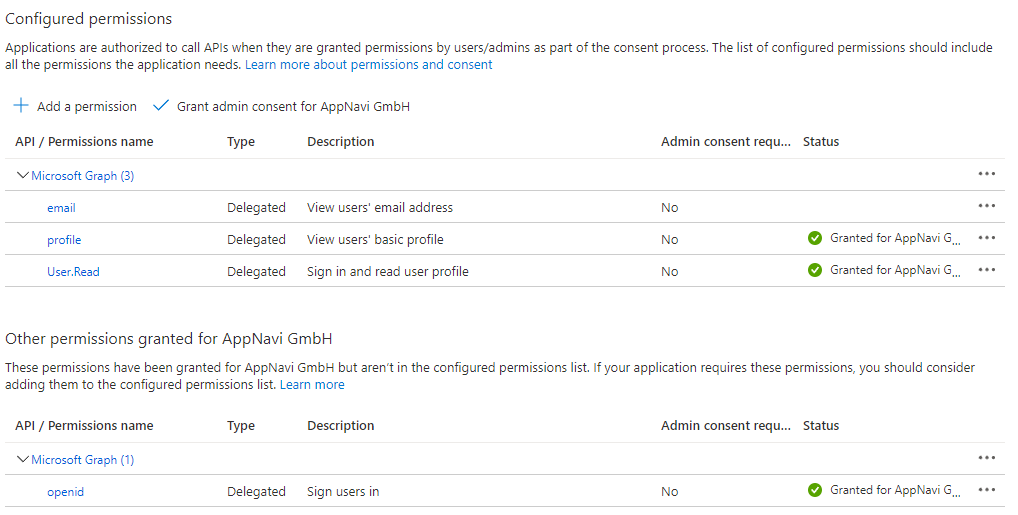
- The following tokens must be issued for AppNavi:
- family_name
- given_name
Step# 2 Copy URIs in the AppNavi Settings
- In the AppNavi portal, go to the Settings page in Manage Tenant tab and enable Single Sign On on the Settings tab.
- In the AppNavi portal, open the OAUTH tab.
- Now open the new application that you have created in Microsoft Entra, go to the Overview and click on Endpoints.
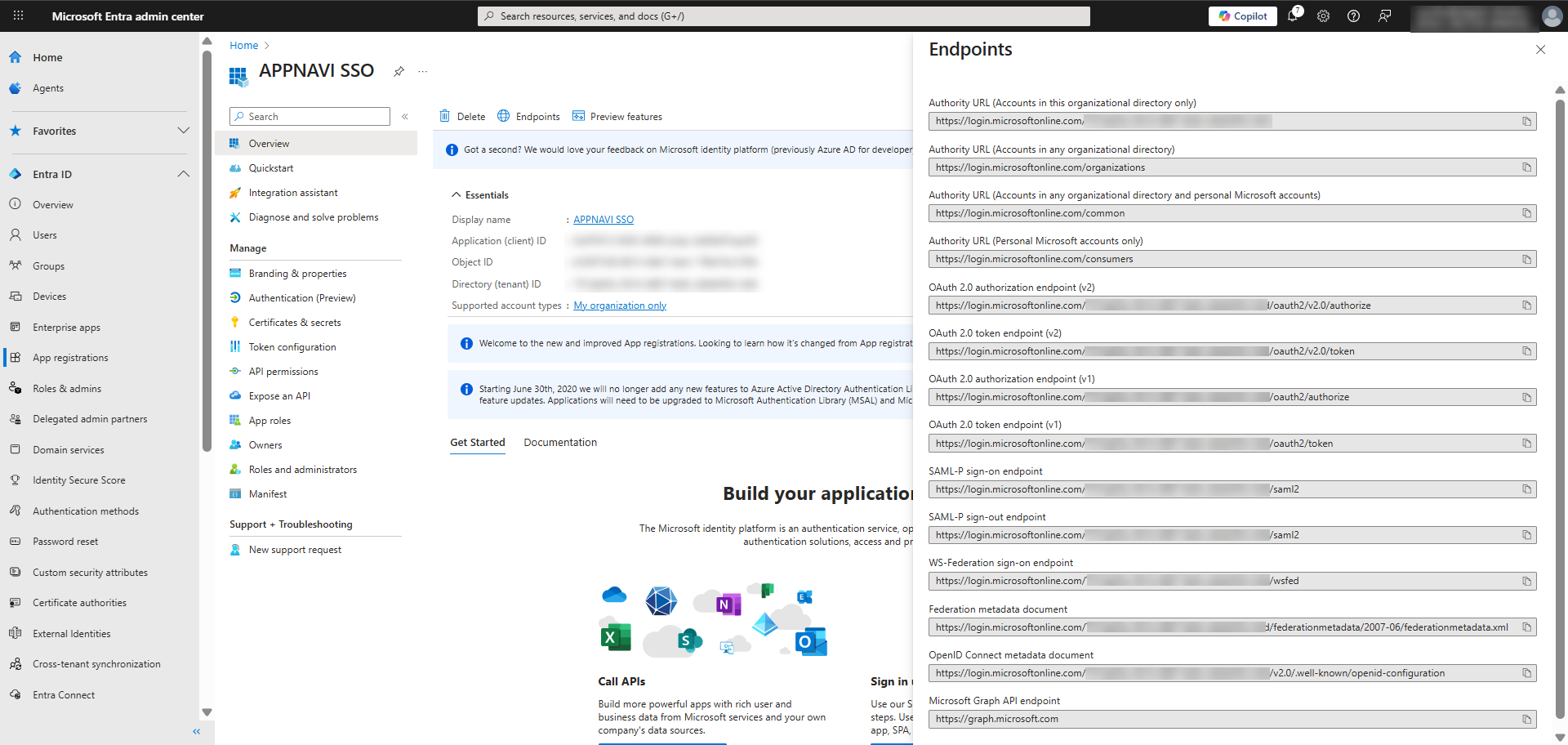
- Copy the value in the OAUTH 2.0 authorization endpoint (v2) field.
- Paste the value that you copied earlier from the OAuth 2.0 authorization endpoint (v2) field into the Authorization URI field.
- Return to Endpoints in Azure AD. Copy the value in the OAuth 2.0 token endpoint (v2) field.
- Return to the AppNavi portal, paste the value into the Token URI field.
- Under UserInfo URI, select "GET" from the drop-down menu and paste the UserInfo endpoint "https://graph.microsoft.com/oidc/userinfo" into the field. The Skip reading entities from ID token and Add data to the query string checkbox is selected by default. This means that user information, specifically the user email address, will be read upon login from the UserInfo URI instead of the token URI.
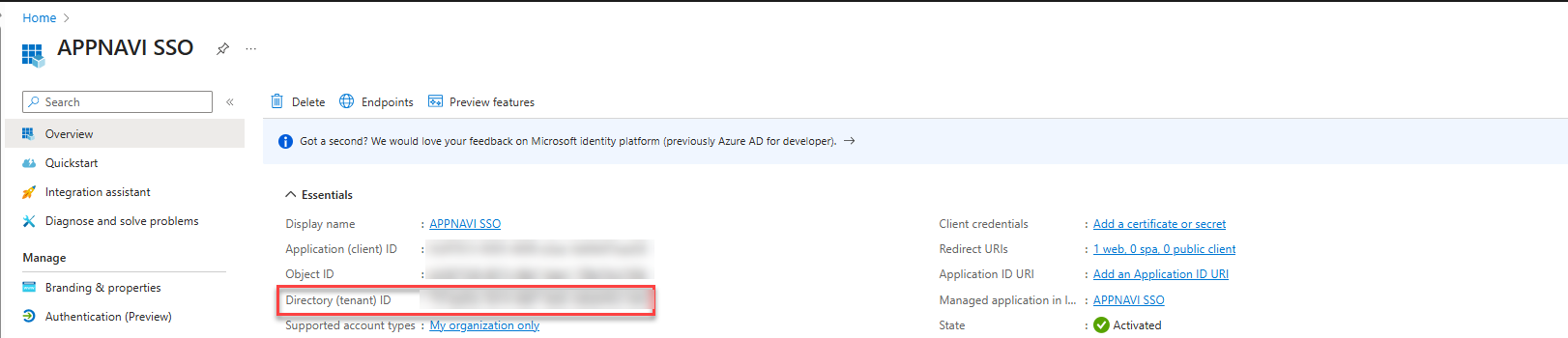
- The Issuer URI for OpenID Connect in Azure AD will typically follow the format “https://login.microsoftonline.com/{tenant-id}/v2.0”. The Client Id can be copied from the Overview of the Application in Entra.
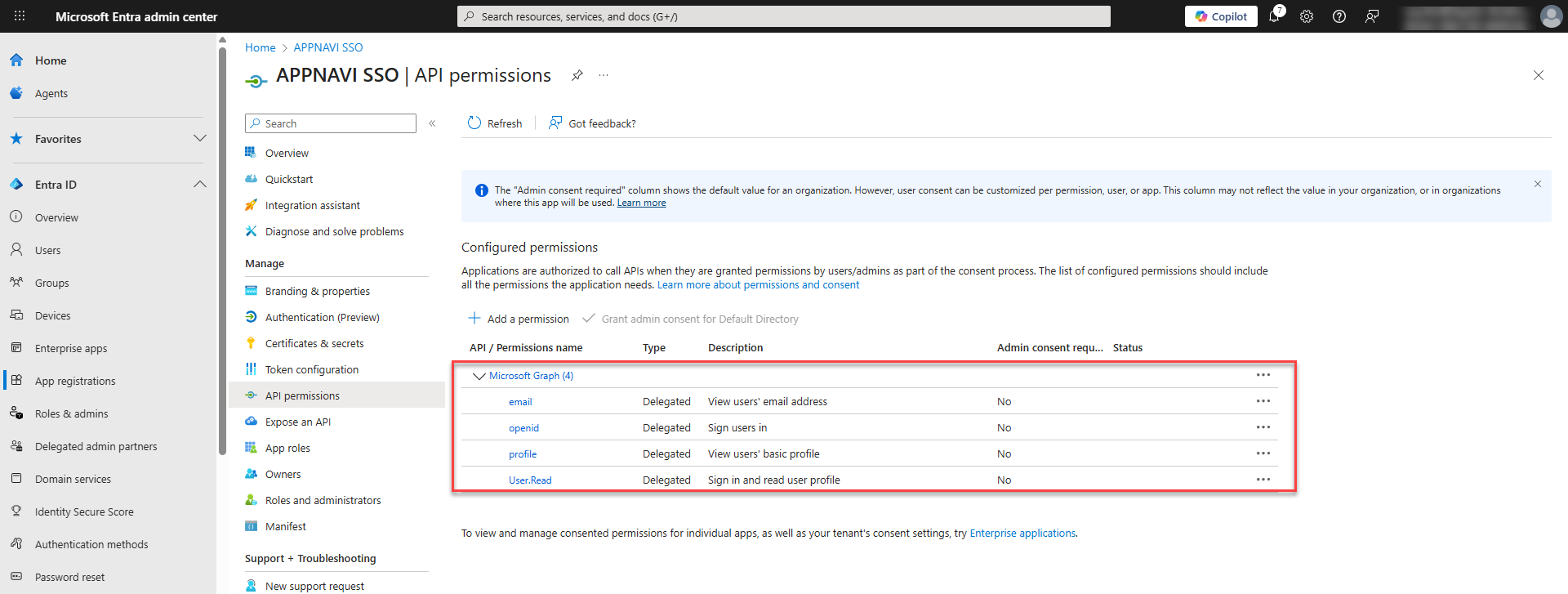
- Under Scopes, enter "openid, email".
Step# 3 Register a new Client Secret
- In the application that you have created in Microsoft Entra, go in the Manage list and click on Certificates & Secrets.
- Select Client secrets.
- Then click on Add new Client secret.
- In the Description field, enter a name for the client secret and choose the relevant expiry date from the Expires drop-down menu.
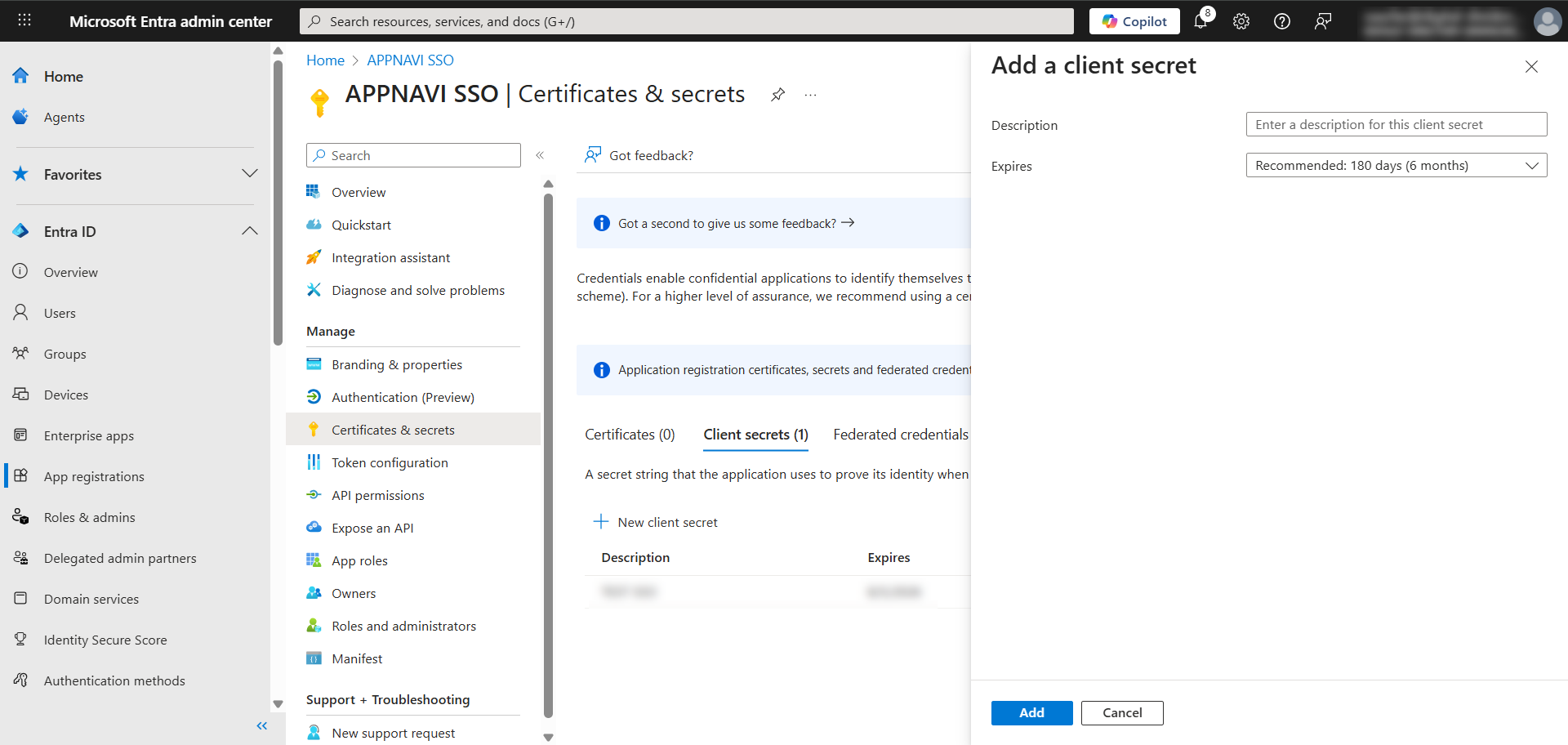
- Click on the Add button.
- A page is displayed showing an overview of the application credentials. Copy the value listed under the Value column.
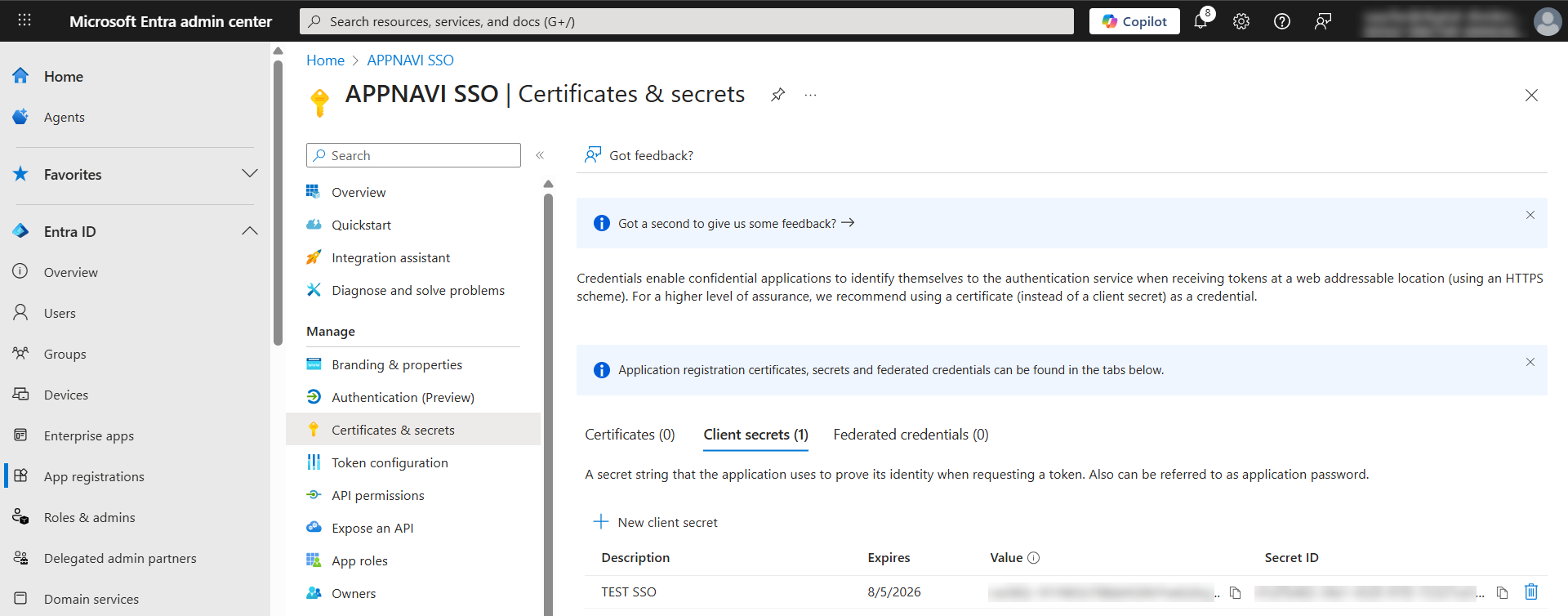
- In the AppNavi portal open the OAUTH tab.
- Now paste the value that you copied earlier into the Client secret field.
- Return to Microsoft Entra and open the Overview. Copy the value that is listed for the Application (client) ID.
- Return to the AppNavi portal. Paste the value into the Client ID field.
Step# 4 Select the Claim
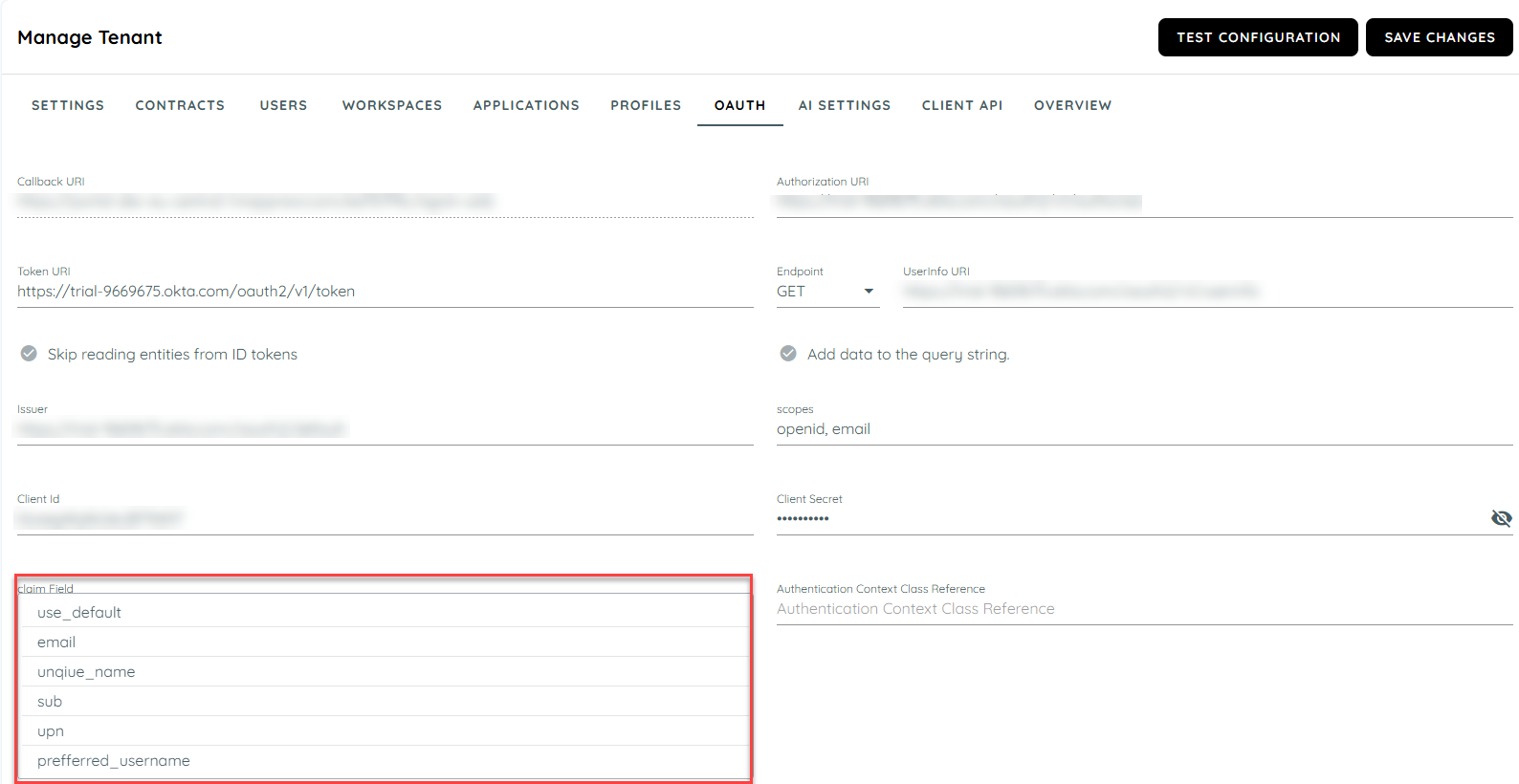
Under the Claim field, select the field in Microsoft Entra where the email addresses of users are stored. To validate that a user exists in AppNavi, the value will be checked if it is in the field that corresponds to the email address used in AppNavi. Depending on your setup in Entra, you can choose between "email", "unique_name", "sub" and "upn".
Step# 5 Review and test
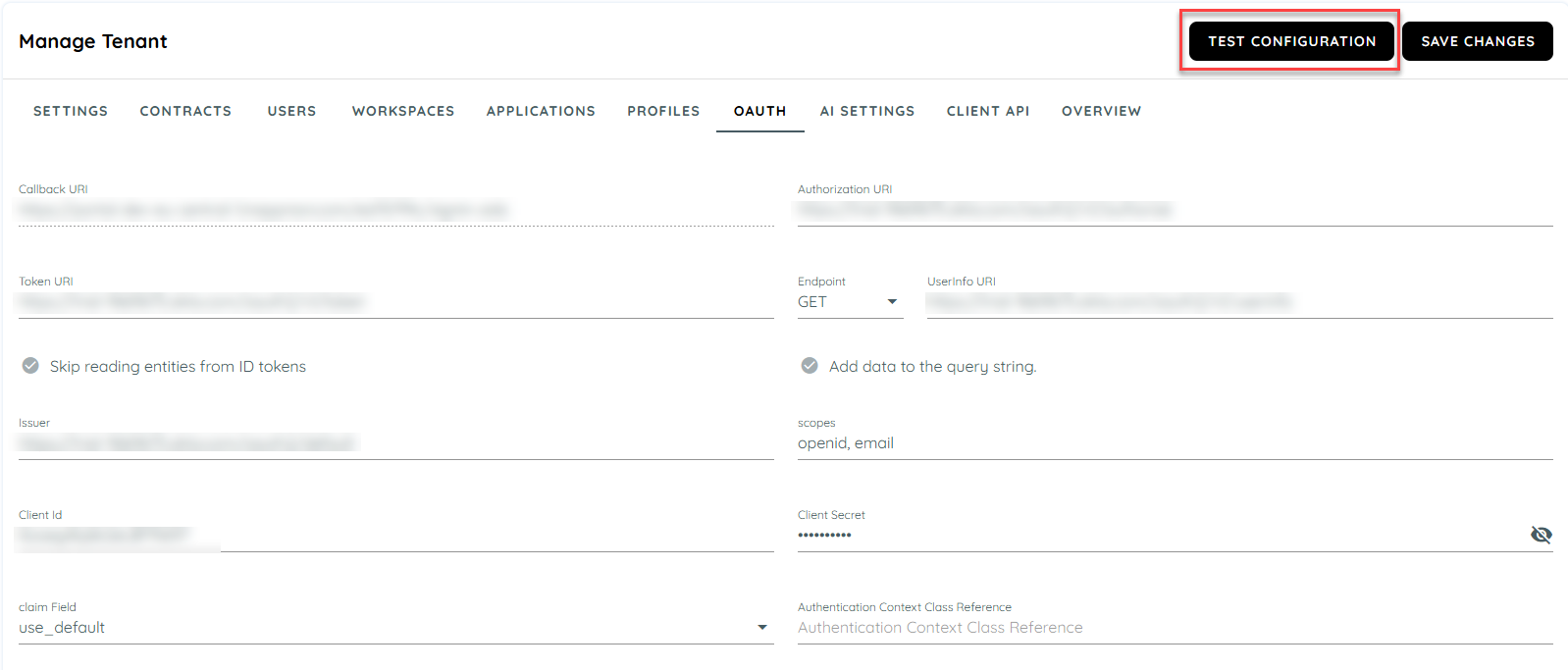
- Review the data that you have entered in AppNavi portal in the OAUTH tab.
- When you are certain that you have entered all the data correctly, click Save Changes to save the data.
- To test the OAuth connection, click Test Configuration.
A user will be redirected to Microsoft Entra. If there are errors, a message will be shown.
To be able to use SSO, users need to have user profiles in both Microsoft Entra ID and AppNavi. The email address that is entered in Entra in the field you have selected under the Claim field must match the email address used in AppNavi.
Updated 3 months ago