SSO
Overview
SSO Usage Tracking is a Discovery feature that shows how much each discovered application uses Single Sign-On (SSO) for login. It detects which identity providers (IdPs) are used and records login events for analysis.
This feature helps organizations see SSO adoption clearly, without changing any existing event data or login flows.
Why This Feature Is Used
Understanding SSO adoption is vital for security and compliance teams. It allows organizations to:
- Know SSO adoption: See which applications are using secure login with SSO.
- Identify providers: Find out which IdPs are being used most.
- Monitor security: Make sure logins happen through trusted identity systems.
- Plan improvements: Understand usage trends to improve SSO adoption.
This feature provides a simple and standardized approach to track authentication methods at scale, helping organizations move toward centralized identity management.
How It Works in AppNavi
When SSO Usage Tracking is enabled, the Discovery feature evaluates event patterns that match valid authentication flows. Only complete flows where a user session transitions from an application to an identity provider and then back to the same application are considered valid.
- Discovery checks login events on already discovered applications.
- If a user logs in using SSO, the system records the event.
- Discovery identifies the IdP and client ID for that login.
- The system counts SSO events and calculates the SSO Usage Index:
This ratio is normalized into an SSO Usage Index and displayed in the Discovery table and dashboards. The following logic is used for normalization:
| Priority level | Meaning |
|---|---|
| Low | Minimal use of SSO |
| Medium | Partial use of SSO |
| High | Strong SSO adoption |
Purpose of This Feature
The goal is to give clear insight into which discovered apps use SSO and how often. This helps with:
- Security checks: Make sure users log in via trusted IdPs.
- Usage reports: See trends and adoption rates.
- Better planning: Decide where to encourage SSO adoption.
No passwords or sensitive data are saved. Only SSO login events and provider information are recorded.
How to Configure
- Navigate to the Discovery Overview page within the portal.
- Click on the three-dot (⋮) menu to open the settings panel.
- Enable the SSO Usage Tracking toggle.
- Save the changes.
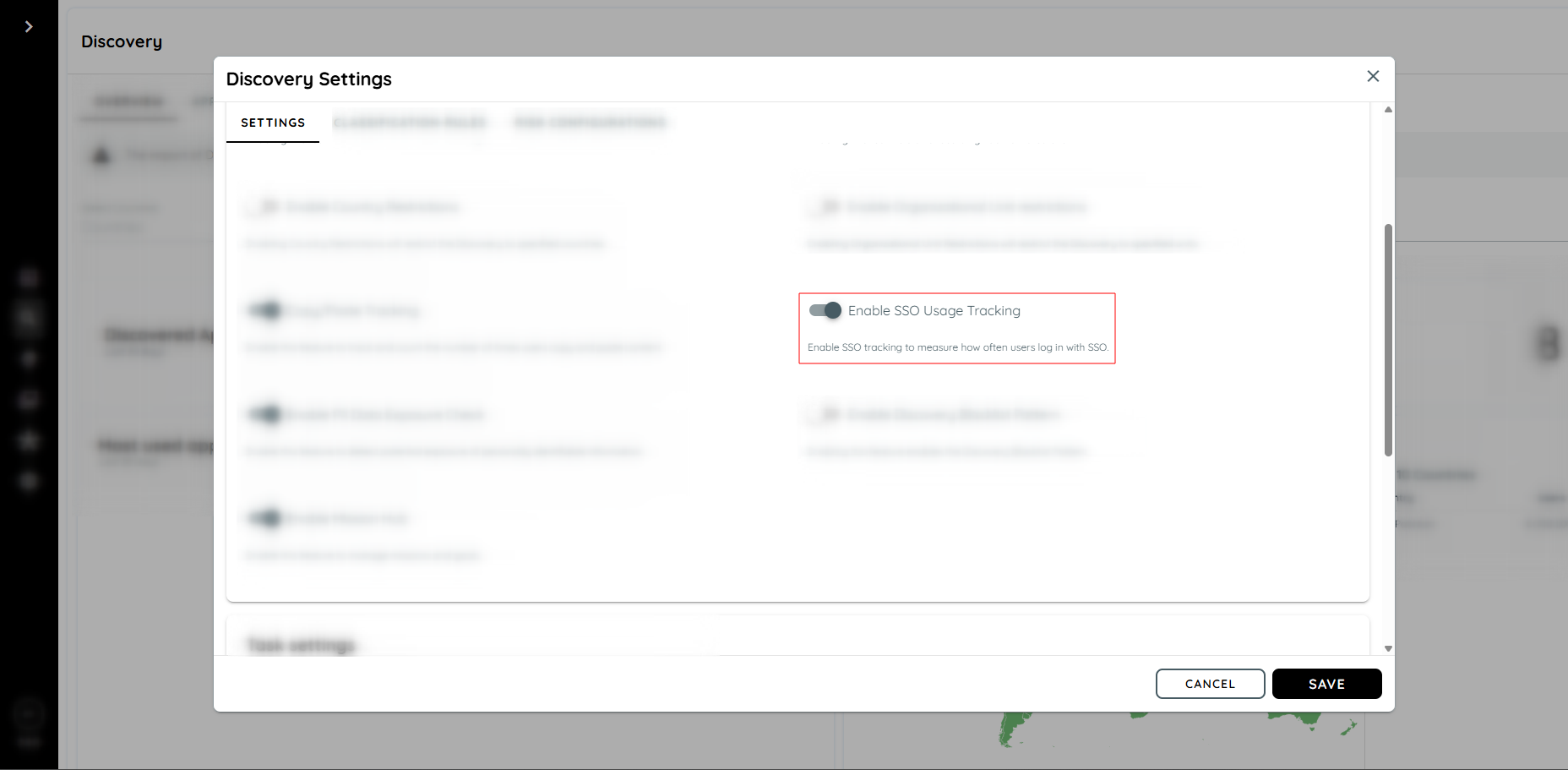
Enable SSO Provider
Once enabled, Discovery begins analyzing authentication flows for detected applications. When users access applications using SSO, corresponding events are captured automatically.
Supported Identity Providers
The feature currently supports the following identity providers:
- GitHub
- GitLab
- Microsoft
- Auth0
- Azure B2C
- Okta
- Amazon Cognito
- Keycloak
- Ping Identity
The architecture allows new providers to be added easily through future updates.
Example Scenario: Tracking SSO Usage in Discovery
An organization enables SSO Usage Tracking to understand authentication adoption across its internal applications.
Steps
- Enablement
In the Discovery overview, the administrator activates the SSO Usage Tracking toggle and saves the configuration.
- Event Capture
- A user accesses an application integrated with AppNavi.
- The user logs in through an identity provider such as Okta or Google.
- Discovery detects a valid SSO flow (App → IdP → App) and enriches the event with provider name and client ID.
- Data Aggregation
- Over time, Discovery aggregates login data and calculates the ratio of SSO logins to total app logins.
- The ratio is normalized into an SSO Usage Index (Low, Medium, High).
- Visualization
- Discovery table shows a new SSO Usage column.
- Hovering over it shows a tooltip, e.g., “72 of 120 user–app–days with SSO (60%) in last 30 days.”
- Provider breakdown is also shown, e.g., “Entra 70%, Google 30%.”
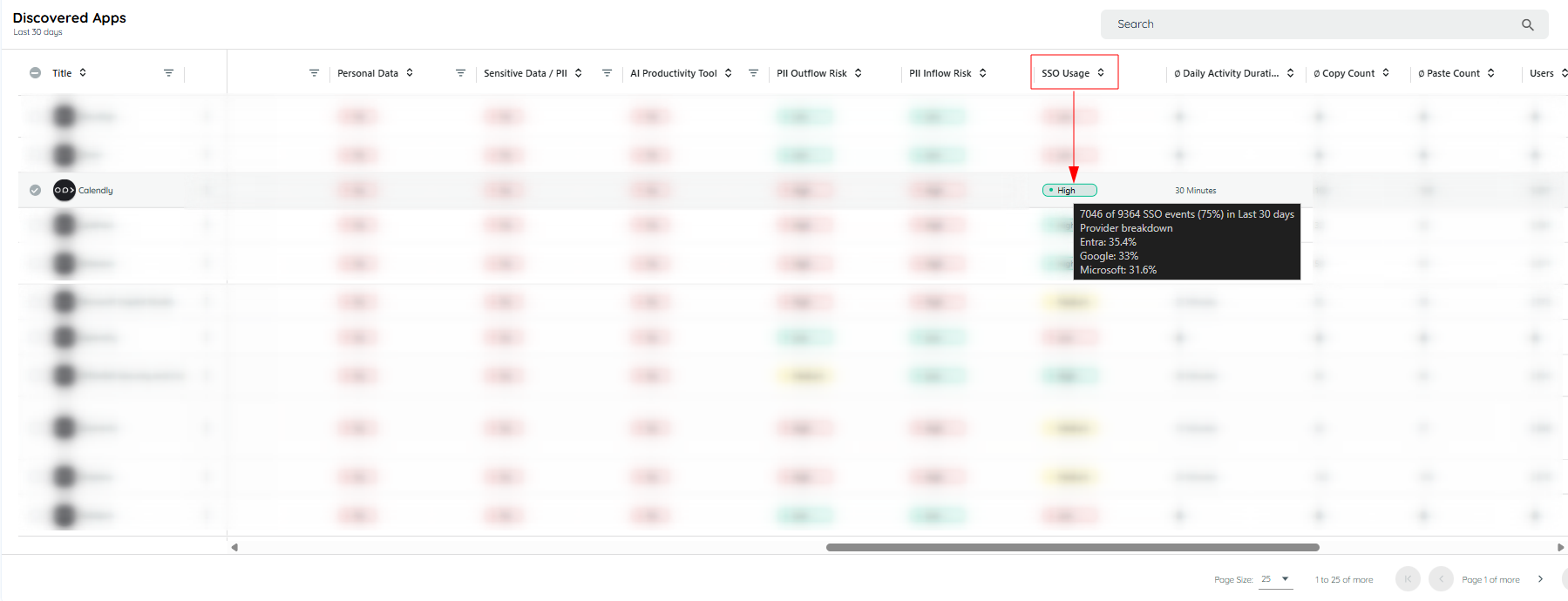
Hovering on the SSO chip
Clicking on the SSO Usage chip opens a dialog that lists all identity providers used, along with their respective percentages.
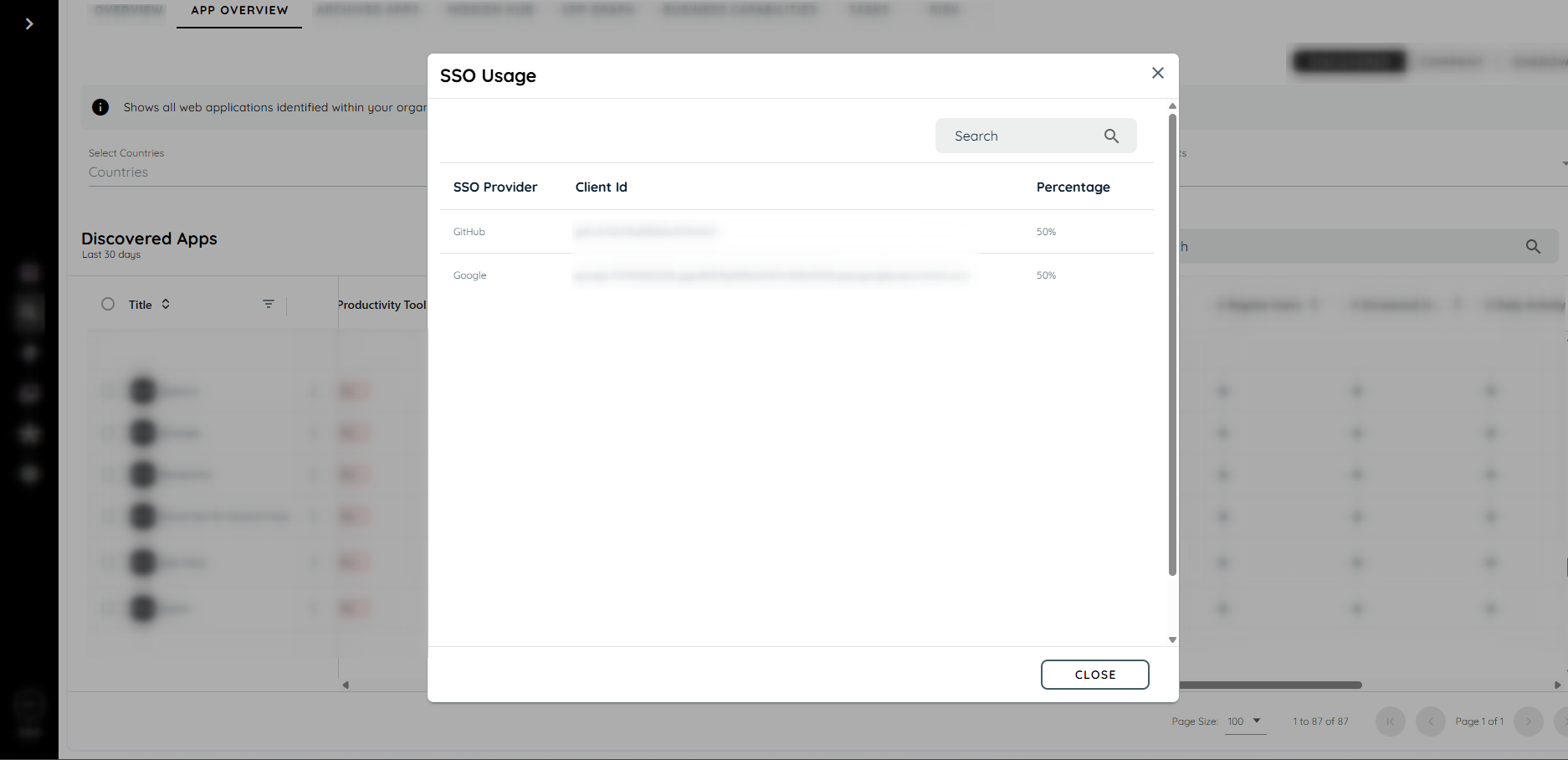
SSO information dialog
Summary
SSO Usage Tracking helps see which discovered apps use SSO and how often. It shows trends, provider usage, and an easy-to-read SSO Index. This improves visibility, security, and planning for login adoption.
Updated 3 months ago